The complexity of cloud technology presents security challenges that traditional security tools can only sometimes solve. Managing cloud security has become crucial with the increasing adoption of cloud technology in various industries.
The cloud has no defined boundary, so conventional security techniques are only sometimes effective. Moreover, manual security procedures often need to be faster and easier to implement at the scale of cloud operations. Additionally, the lack of centralization makes monitoring and ensuring security in complex cloud environments with multiple accounts challenging. Knowing that even a single misconfiguration can have disastrous outcomes is important.
What are the reasons behind cloud security misconfigurations?
Misconfigurations in cloud security happen due to the need for proper controls to be put in place for applications, containers, infrastructure, and other software elements. This can result from organizations not having complete visibility into their infrastructure and how containers, Kubernetes, and cloud services interact. Additionally, using the default security settings or credentials, often inadequate from a security perspective, can contribute to misconfigurations.
3 Main reasons for cloud misconfigurations
Lack of cloud security information, expertise, and clear view
Delay in the detection of cloud threats and remediation of cloud misconfigurations
Lack of alignment between SecOps and developers teams.

What Misconfigurations in the Cloud Can the CSPM Platform Identify?
As organizations grow and adapt to changing cloud infrastructure, they may transfer processes from one cloud to another or adopt a multi-cloud environment. This can result in losing track of data and assets, like misplacing items during a move. This lack of visibility in the cloud can create security risks, including an unknown attack surface, mainly if employees use unauthorized cloud services (shadow IT).
CSPM offers a solution to this challenge by conducting scans to identify all cloud assets and providing a clear understanding of their status. It also informs security teams of misconfigurations in the discovered assets, improving visibility and reducing security risks.
Here are some examples of the common cloud misconfigurations that CSPM can detect
Incorrect configuration of multi-factor authentication for all users.
Accidental disabling of CloudTrail, which prevents logging of events.
Public-facing S3 buckets that are not protected.
Compute instances with vulnerabilities in their applications.
Excessive account permissions.
No multi-factor authentication is enabled on critical accounts.
Misconfigured network connectivity.
Data storage is exposed directly to the internet.
Compliance drift.
Why is CSPM essential for an organization's growth?
CSPM tools provide real-time monitoring and alerting, enabling organizations to detect potential security threats and respond promptly. Moreover, these tools offer automated remediation capabilities, making it easier for organizations to resolve security issues without manual intervention.
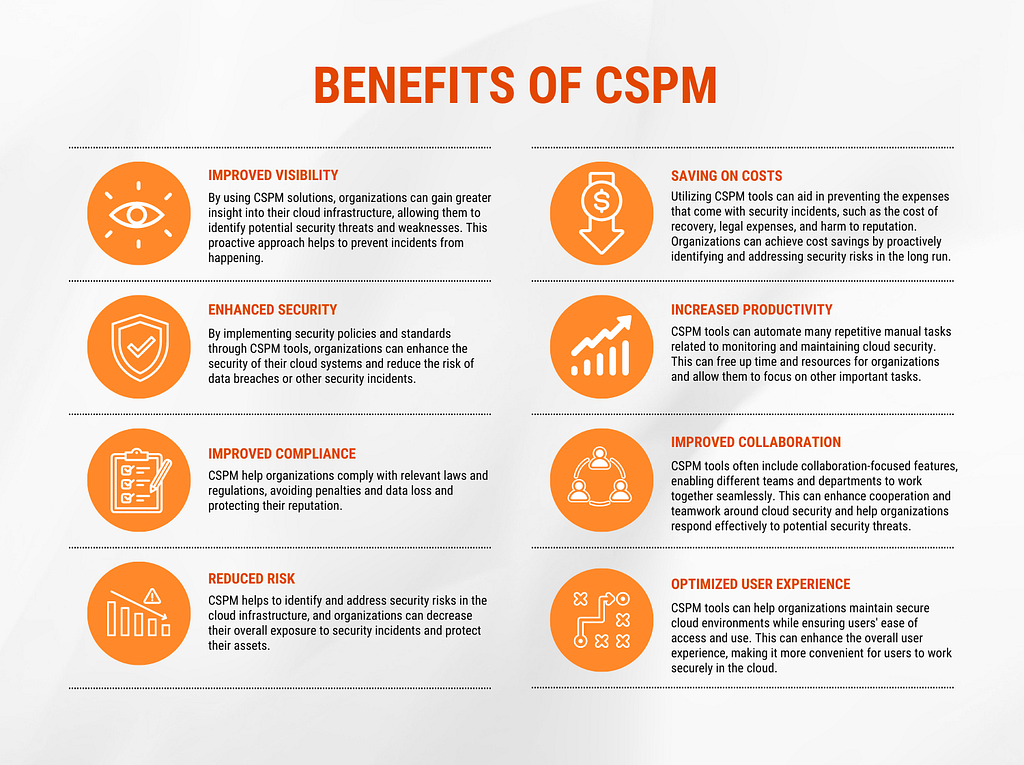
CSPM tools are specifically designed to enhance an organization's cybersecurity posture. It gives organizations visibility into businesses cloud systems, helping to identify potential security risks and providing guidance on how to address them. This not only helps organizations protect their sensitive data and systems from threats, but it also helps prevent data breaches and other security incidents. In short, CSPM tools are crucial for organizations to ensure the security and compliance of their cloud-based resources with industry standards and regulations. Below are reasons why organizations need comprehensive CSPM tools.
Identifying and Automating Correction of Cloud Configuration Issues - One of the core functions of CSPM is to identify misconfigurations based on cloud provider standards. This is important as even a simple misconfiguration, like an unencrypted S3 bucket, could result in a security breach. A CSPM solution can provide a list of misconfigurations, making it easier to manage at scale, where cloud architectures can be complex.
Visual Representation of All Cloud Services - CSPM can provide a visual map of all cloud services. This makes it easier to understand the interaction of different services, objects, etc and provides a better understanding.
Detection of Changes in Cloud Infrastructure - CSPM solutions can also identify cloud infrastructure drift, occurring unexpectedly when the architecture changes. This is important as it helps businesses respond quickly to unapproved changes, maintain the approved architecture, and ensure the infrastructure remains secure and compliant.
Centralized Cloud Service Information - Continuous monitoring of cloud infrastructure is also a key function of CSPM solutions. These solutions provide a holistic and ongoing view of the enterprise cloud infrastructure, reducing the risk of misconfigurations and eliminating the risk of human error.
Assessing Risk in Data Storage - CSPM identifies data risks associated with cloud storage components. It ensures that the storage components are properly configured and encrypted and that it is not publicly accessible. This helps businesses minimize the risk of data breaches and maintain the security of their cloud infrastructure.
Enforcing Policy Compliance - Automating policy violations is another important feature of CSPM solutions. This allows businesses to respond quickly to unexpected events and to understand what is happening and why.
Streamlining Cloud Provisioning - CSPM solutions also support cloud provisioning automation using technologies like Terraform and CloudFormation. This allows businesses to update their cloud infrastructure with a single click, making it easier to maintain security and compliance.
Managing Account and Role Access Controls - CSPM monitors accounts and role permissions to ensure that users and roles have the least privileges required to perform their tasks. This helps minimize the risk of overprivileged users or roles, improving the security of the cloud infrastructure.
Shared responsibility and CSPM
The concept of shared responsibility is crucial to developing a successful Cloud Security Posture Management (CSPM) strategy. It involves the division of responsibilities between cloud service providers and their customers in securing cloud environments. The cloud providers are responsible for securing physical access to the cloud infrastructure and the bare-metal servers. At the same time, the customers are responsible for securing the workloads they deploy within the cloud.
To aid customers in securing their cloud environments, public clouds offer tools such as IAM frameworks and virtual networking configurations. However, it's up to the customers to use these tools correctly. This is where CSPM steps in, as it helps customers ensure that their cloud configurations align with security best practices and compliance rules. CSPM helps customers secure cloud environments by automatically scanning configurations for security risks.
What type of CSPM tool should businesses choose?
To get complete visibility and information on where an organization's most critical vulnerabilities are, Here are some factors to consider when choosing a CSPM tool:
Choose a CSPM tool that comprehensively views multi-cloud infrastructure, including real-time visibility into security issues and detailed reporting capabilities.
The tool can make immediate remediations through automation features without human intervention.
A CSPM tool that is easy to use and set up can ensure that it is adopted and used effectively by the security team.
Choose a tool that can Oversee, evaluate, and control IaaS, SaaS, and PaaS platforms in both on-premise, hybrid cloud and multi-cloud surroundings.
Some CSPM tools offer customization options to meet the organization's unique needs, so consider whether you need this level of customization before making a decision.
Detecting and rectifying cloud misconfigurations automatically.
Preserving policy transparency and ensuring consistent enforcement across all service providers.
Checking for updates in regulatory compliance regulations such as HIPAA, PCI DSS, and GDPR and proposing new security standards.
Conducting risk assessments based on frameworks and external standards established by the organizations such as GDPR, CSA, ISC, ISO, etc.
