Securing Your Cloud-Native Applications with CNAPP: The Comprehensive Solution
Cloud Native Application Protection Platform (CNAPP) is a new breed of security solution designed to protect cloud-native applications. It is specifically tailored to address the unique challenges cloud-native applications face, which are built using modern development methodologies such as DevOps, agile, and microservices architecture. CNAPP is a comprehensive platform that offers multiple layers of protection to secure the entire application stack, including the application, infrastructure, and data.
In this article, we will explore the key features and benefits of CNAPP, how it works, and why it is essential for organizations looking to secure their cloud-native applications.
Why is the Legacy approach starting to fail?
As businesses expand, they often accumulate a variety of technologies, leading to different security controls across multiple cloud environments. To secure cloud infrastructure and production environments, security teams employ various tools such as CSPM, CIEM, and CWPP. However, due to its complexity, this approach can make it challenging for them to concentrate, rank, and resolve risks efficiently.
There are gaps in visibility and blind spots in security due to multiple data sources and no reliable source of truth.
There is an overwhelming amount of data, and correlating it takes much time.
It's easy to become desensitized to alerts and miss critical issues that require attention.
There are a resource, technical knowledge, and training limitations for each tool.
Managing multiple tools separately results in high operational complexity and overhead.
Maintaining proper controls using disparate tools in complex environments requires significant time, resources, and manual effort, which may need to be improved.
Why Consolidated Solutions for Cybersecurity is the answer?
As cybersecurity needs continue to diversify, managing multiple corresponding solutions can become complex and inefficient. The need for more visibility and the need to exchange information between different platforms can overwhelm security teams and increase the risk of errors. A consolidated approach, where all elements are integrated into a unified solution, can provide a smarter solution to this problem. This approach, known as CNAPP by Gartner, offers comprehensive application protection in the cloud environment and takes a more holistic approach to cybersecurity by considering interconnected issues rather than individual problem points.
Why Do Businesses Need CNAPPs?
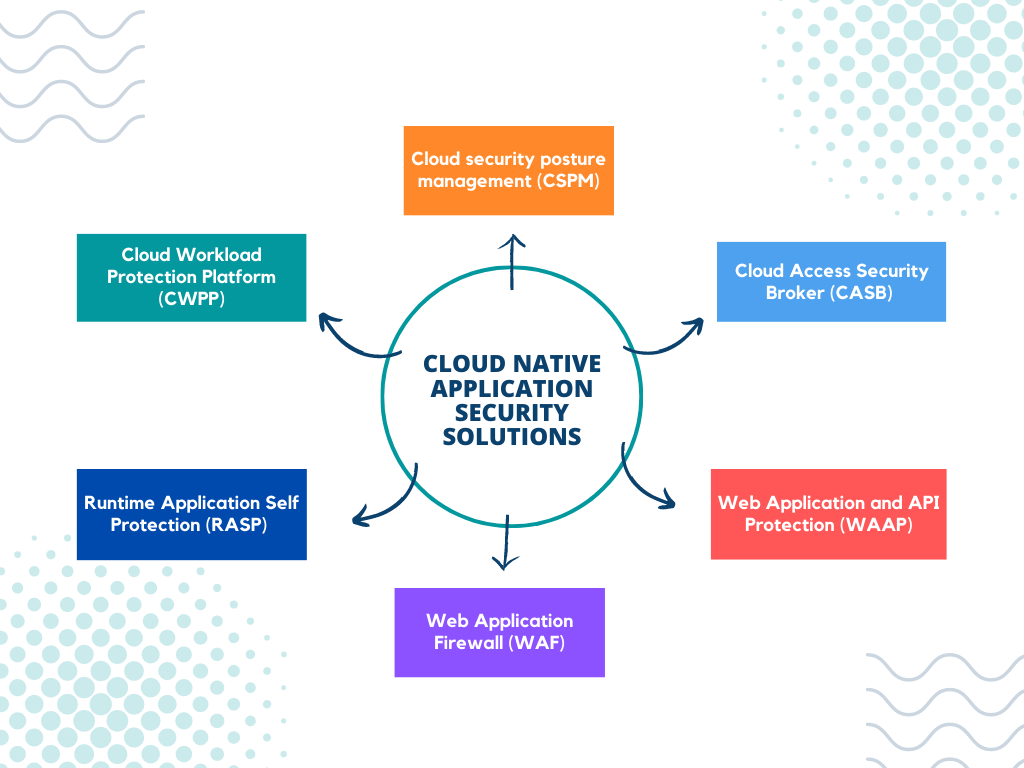
While adopting cloud-native applications has brought many benefits to businesses, such as enhanced scalability, agility, and cost-effectiveness, it has also introduced new security challenges. These highly dynamic applications undergo continuous changes, which traditional security solutions struggle to keep up with. To overcome these challenges, CNAPPs provide a purpose-built, comprehensive security solution. They offer complete visibility and control over the entire application development and deployment pipeline, ensuring that security is integrated into every process stage. Furthermore, CNAPPs provide real-time protection and response to threats, ensuring the continued security of applications even as they scale and change.
Dynamic and transient nature of cloud-native environments: Cloud-native applications are designed to run on containerized environments, where containers can be spun up or down in seconds, and new instances can be created automatically in response to traffic spikes or failures. This dynamic nature of cloud-native environments makes it challenging to maintain a consistent security posture across the entire application stack. A CNAPP can provide visibility and protection across all containers, microservices, and API endpoints, ensuring that security policies are enforced consistently.
Microservices architecture: Cloud-native applications are typically composed of multiple microservices that interact with each other to perform complex tasks. This distributed architecture increases the attack surface and makes detecting and responding to security threats difficult.
DevOps and continuous delivery: Cloud-native applications emphasizing speed and agility are developed, deployed, and updated using DevOps practices. Traditional security solutions that rely on manual intervention and approval processes can slow down the development and deployment process, making it challenging to keep up with the fast-paced nature of cloud-native environments.
Hybrid and multi-cloud environments: Many organizations are adopting a hybrid and multi-cloud strategy to leverage the benefits of different cloud platforms. However, this approach can also create security challenges, such as inconsistent security policies and a lack of visibility across multiple environments.
Scalability and Resilience - Cloud-native applications must be highly scalable and resilient to handle the demands of modern business operations. CNAPP provides tools and services that make it easy to scale applications horizontally by adding more instances and vertically by increasing the resources allocated to each instance.
Continuous Integration and Delivery - Cloud-native applications are developed using agile methodologies and require frequent updates and deployments. CNAPP provides tools and services that enable developers to implement continuous integration and delivery (CI/CD) pipelines that automate application testing, building, and deployment. This reduces the risk of errors and ensures that applications are always up-to-date.
Security and Compliance - Security and compliance are major concerns when deploying cloud-native applications. CNAPP provides security features that enable developers to secure their applications and comply with relevant regulations. These features include encryption, access control, and auditing, which can help organizations protect sensitive data and ensure their applications are secure.
The Knowledge Gap: More internal knowledge about security is the biggest challenge for securing cloud-native apps in a DevOps pipeline. This knowledge gap can lead to security teams deploying many different point products to address specific needs, creating more work for already stretched teams. Developers are also affected, as the manual correlation between different security products can lead to delays in development workflows and undetected risks throughout the lifecycle.
Collaboration: Collaboration is key to a thriving DevOps culture. It's no longer just about developers versus security professionals. Secure cloud app development requires two-way communication between the two teams. This is particularly crucial as organizations shift towards more complex multi- and hybrid-cloud environments, and the amount of data they handle continues to grow.
Features of Cloud Native Application Protection Platform
Cloud Native Application Protection Platform (CNAPP) is a security solution designed to protect cloud-native applications, typically built using modern technologies such as containers, microservices, and serverless functions. Here are some unique features of CNAPP:
Containerized Deployment: CNAPP can be deployed as a containerized application, which makes it easy to scale and manage. It can run on container orchestration platforms like Kubernetes, Docker Swarm, and Amazon Elastic Container Service (ECS).
Microservices-Based Architecture: CNAPP is built using a microservices-based architecture, where each microservice performs a specific security function, such as vulnerability scanning, threat detection, or access control. This architecture provides greater flexibility, scalability, and resiliency to the security solution.
Cloud-Native Integration: CNAPP is designed to integrate seamlessly with cloud-native environments, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). This integration allows CNAPP to leverage cloud-native services for enhanced security, such as AWS Lambda for serverless computing or AWS CloudTrail for audit logging.
Automatic Security Policy Generation: CNAPP can automatically generate security policies based on the application's behavior and characteristics. This feature helps reduce the time and effort required to configure security policies while ensuring that the policies align with the application's requirements.
AI/ML-Based Threat Detection: CNAPP uses advanced artificial intelligence (AI) and machine learning (ML) algorithms to detect and prevent sophisticated cyber threats. These algorithms can analyze large amounts of data in real-time to identify anomalies and potential security breaches.
Centralized Management and Monitoring: CNAPP provides a centralized management and monitoring console, which allows security administrators to view and manage security policies across multiple cloud-native applications and environments. This feature provides greater visibility and control over security operations.
Compliance and Governance: CNAPP helps organizations to comply with various regulatory requirements, such as PCI-DSS, HIPAA, and GDPR, by providing automated compliance checks and reporting. This feature helps to ensure that cloud-native applications are secure and compliant with relevant regulations.
Best Practices for Secure cloud-native Applications

Implement the least privilege model to ensure that teams have only the minimum access required to perform their roles.
Maintain an inventory of all cloud applications, workloads, and assets to improve visibility across the entire cloud environment and limit the attack surface by removing non-essential applications or workloads.
Audit activities across cloud environments to detect threatening patterns before any negative incident occurs and comply with regulatory requirements.
Categorize sensitive data to apply different policies and restrict access to only user groups with elevated authorities.
Conduct security testing in each environment of an application, as security tests are equally critical as functional testing.
Develop and enforce consistent cloud security policies, frameworks, and architectures encompassing all aspects of cybersecurity, including network, infrastructure, endpoint, and cloud security.
Encourage employees to create secure passwords and change them frequently to protect against phishing attacks.
Use identity access management (IAM) to ensure each user is authenticated and only authorized data and application functions are accessed, and automate managing user identities and access permissions.
Focus on data security by implementing encryption at the platform, database, and application levels to protect data in transit, at rest, and in use.
Use encryption to reduce the risk of cloud applications leaking sensitive data and protect organizations from intellectual property theft, reputation damage, and loss of revenue.
