How to Recognize and Protect Against Phishing Emails: Real-World Examples and Reporting Tips
Phishing scams and emails can be very harmful. Phishing emails are difficult to recognize, appear genuine, and may have grave repercussions. This article will cover real-world phishing cases, reporting phishing emails, and how to deal with phishing emails.
What are Phishing Emails and scams?
Emails that appear and pretend to be from a particular person or business but are false are known as phishing emails. In the business world, a regular vendor may send you a phishing email alerting you that their banking information has changed. Your business makes the payment but gets stolen in the phishing scam and never gets to your legitimate vendors.
Another well-known example is an Amazon phishing email that claims, "Your account has been suspended." Reactivating your Account requires you to click a link and enter your information. Once those details have been collected, the attackers may use them for fraud or market them on the dark web.
What makes phishing so dangerous? Over 90% of internet attacks, including ransomware, malware, password theft, and data breaches, result from phishing emails and attacks.
Real World Example of common phishing emails
While phishing emails can cause severe damage, the good news is that you can identify a few common red flags to order falling prey to a phishing attack.

These phishing email examples will demonstrate the most frequent phishing email red flags and assist you in recognizing actual phishing emails.
1. Google Doc scam - The Google Docs scam, one of the most current and prominent phishing attacks, has an additional dark twist because the sender is frequently someone you know. Despite Google's efforts to contain it the scam is still prevalent.
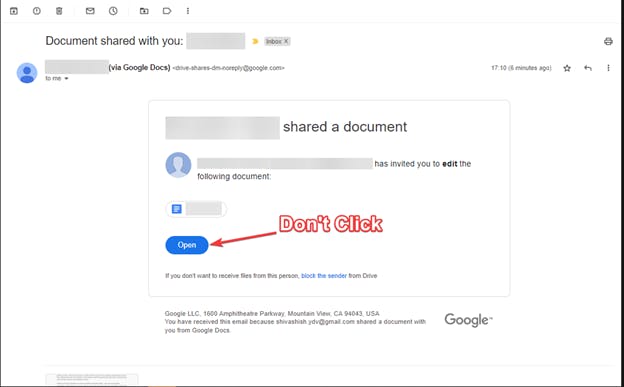
This brilliant email invites you to click on its link to open a doc, redirecting you to a page that looks almost exactly like the login page for Gmail. The attacker gets complete control when you accept the invitation to allow access to your Google account after a particular document has been chosen.
2. PayPal Scam - PayPal has almost 200 million members and is a highly profitable platform for online criminals. Criminals and hackers try to access the platform directly to lure users to get credit card or bank account information. Phishing emails are being sent by scammers in 2022 using legitimate PayPal accounts.

3. HR Email Scam - A HR email scam often contains a malicious attachment or link that, once clicked, will install malicious software onto your computer or device. You should encourage colleagues to ask the HR sender whether a request for personal information is legitimate.
Cybercriminals perpetrated on unsuspecting victims by sending them phishing emails that claimed to be from their individual employer's human resources department.

4. Unusual activity scam - Victims are not just confronted with haste and terror. Alarms go out as soon as you get an email or text notifying you that there has been "strange activity on your account." Because of the victims' uncertainty, this con works effectively for hackers. Phishing emails with unusual sign-in activities are sent to Microsoft account holders in February 2022.

How to Protect Against Phishing Attacks
Your email spam filters might block many phishing emails in your inbox. However, spam filters are constantly being outsmarted by scammers, so adding further layers of security can be helpful. Here are 4 methods for defending against phishing scams.
Four Strategies To Guard Against Phishing:
Use antivirus to shield your machine. Set it to update to respond to any new security risks automatically.
Set software updates to occur automatically to protect your device. You may receive important security threat protection from these upgrades.
Make use of Multi-Factor Authentication to safeguard your accounts. For example, some accounts require two or more login credentials.
Make a backup of your data to protect it. For example, your computer's data should be backed to the cloud or an external hard drive. Additionally, back up the info on your phone.

If You Responded to a Phishing Email, What to Do
You can mitigate the harm by knowing what to do after a successful phishing attack. Here are some actions you should take if you believe you've been the target of a phishing email.
Report Phishing emails immediately - Phishing attacks should be reported to your IT service desk or in accordance with your company's cyber incident response procedures (CIRP). The information security team can begin gathering information about the attack with the help of an immediate report of the incident.
Change your password - Change the password before it is compromised.
Examine the Phishing attack - Always try to cross-check how much the attack is severe.
Inform the essential law enforcement and regulatory agencies - Depending on the extent of the harm done. It might be necessary to submit a case to the appropriate law enforcement organization, like IdentityTheft.gov or IC3.
Talk to your IT team about remediation strategies - Organizations should ensure staff is informed on the techniques attackers will likely use to stop more attacks.
Raise cybersecurity awareness - To ensure employees are prepared, provide them with thorough security education and training.
Ways For Reporting Phishing
Report any phishing emails or texts you receive. The details you provide aid with the battle against fraudsters. In order to prevent consumers from falling for phishing incidents, different countries have cyber crime departments. For example, US-CERT collaborates with the Anti-Phishing Working Group (APWG) to gather phishing email messages and website addresses to take action.
Phishing can be reported to these authorities by emailing to the appropriate department.
Send the phishing email you received to the government cyber crime department if you received one.
Send any phishing text message you receive to spam and report it.
Notify the government authorities by calling them about the phishing attack.
