Data Security Posture Management (DSPM): The Key to Effective Cloud Data Security
Table of contents
- The Challenge of Data Security in Enterprises
- Limitations of Traditional and CSP-Native Solutions for Cloud Data Security
- Exploring the Limitations of Traditional and CSP-Native Solutions
- A modern approach to data security that represents the latest evolution
- Why DSPM is the Only Viable Option for business security
- Benefits of Deploying DSPM in an Organization
- What type of DSPM solution should businesses choose?
Data Security Posture Management (DSPM) is a novel approach to securing cloud data that prioritizes data protection. DSPM recognizes that data is the most valuable asset of any organization. In modern multi-cloud environments, the vast amount of data increases the risks of data loss or compromise. This is why cloud data security has become the primary concern for security stakeholders, especially those relying on outdated security strategies.
DSPM offers a contemporary approach to comprehending all the factors affecting the security posture of business data. By utilizing the guidelines and platform-based instrumentation of DSPM, organizations can efficiently locate sensitive data in the cloud environment, identify who has access to it and assess its security posture. By following DSPM, an organization can quickly and effectively protect its data.
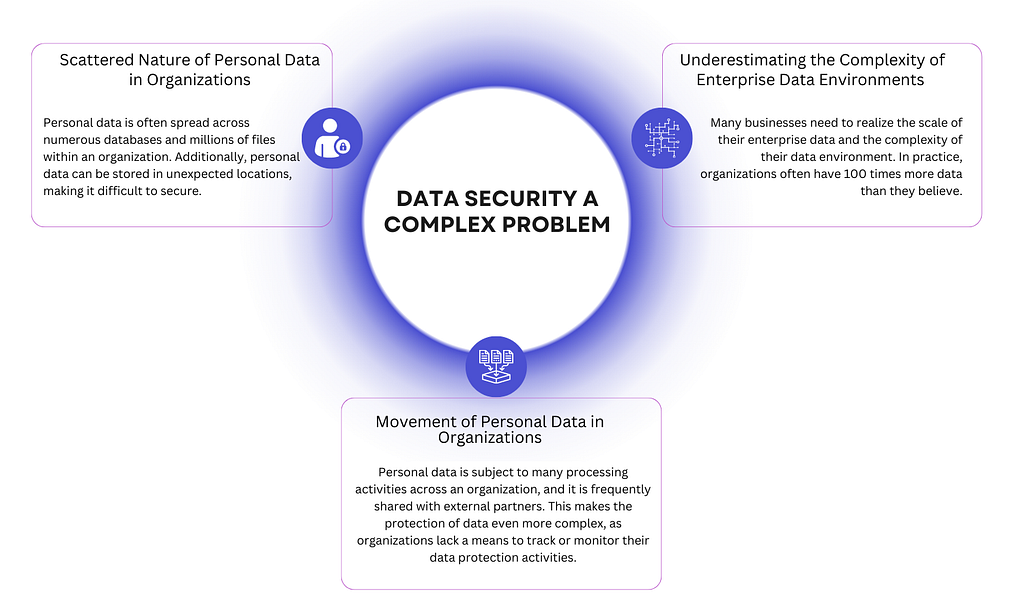
The Challenge of Data Security in Enterprises
As the amount and complexity of data continue to increase within organizations, ensuring data privacy and security has become challenging. The protection of data in enterprises has become a multifaceted problem.
Limitations of Traditional and CSP-Native Solutions for Cloud Data Security
The rapid growth and evolution of cloud data have outpaced the capabilities of traditional data security solutions. As a result, a Security Execution Gap has emerged, where security teams lack the tools and expertise to protect cloud data effectively. This gap limits the ability of cloud data practitioners to create value quickly and safely, putting organizations at a competitive disadvantage. In this context, it is crucial to explore the limitations of traditional and CSP-native solutions to understand why DSPM is the only viable option for effective cloud data security.
Exploring the Limitations of Traditional and CSP-Native Solutions
Traditional and CSP-native solutions have limitations that are inadequate for cloud data security. Traditional solutions are not designed to handle cloud data's massive scale and distributed nature. It also needs to be better equipped to manage the dynamic nature of cloud data, which is constantly changing and evolving. On the other hand, CSP-native solutions are built to protect the cloud infrastructure but not necessarily the data stored in it. It cannot identify, classify, and protect sensitive data, which is critical for compliance with data protection regulations. Additionally, both traditional and CSP-native solutions are reactive, requiring manual intervention to address security incidents, which can result in delayed responses and increased risk exposure.
Manual:
The dynamic nature of the cloud is a challenging environment because changes happen so rapidly that data inventory can become outdated within minutes.
Security is unable to detect "shadow" data.
Lacks the capability to track and properly monitor the most valuable and sensitive data assets.
There is a lack of ability to easily understand the exposure level of individual data elements and control access to them accordingly.
Implementing an effective data security solution can require significant in-house engineering efforts.
Cloud provider's native tools:
Many data discovery solutions are limited to a single cloud or have limited support.
Most solutions are per-use and don't offer continuous scanning, resulting in blind spots for unknown or shadow data.
Complete re-scanning is required every time there's a change in data.
Most solutions cannot find shadow data and lack policy alerts, guided remediation, and ongoing monitoring.
The scope of data stores that these solutions can scan is often limited. For example, AWS Macie can only support AWS S3 buckets, which is incomplete for most users. It doesn't scan RDS, EBS, or containers on EC2.
Legacy:
Centralized approaches to data discovery can be expensive to configure and maintain, requiring a list of credentials for all data stores.
Connector/agent-based approaches may not be able to discover unknown or offline data, leading to blind spots in cloud environments.
Connector-based solutions require access to production instances, and scanning should be done asynchronously to avoid affecting performance.
Identifying, configuring, and connecting each data asset can be time-consuming, especially for larger enterprises with thousands of assets, taking months to complete.
A modern approach to data security that represents the latest evolution
In cybersecurity, "Where is our data?" is paramount. It is impossible to secure data until its location is identified, especially if it is critical business, customer, or regulated data. In the current age of agility, data can be stored almost anywhere in the cloud, which makes it challenging to locate. The first step towards securing cloud data is gaining better and deep visibility, which is where Data Security Posture Management (DSPM) comes into play.
There are different types of posture management. However, they all have two common goals: identifying issues and finding solutions. DSPM is a new approach to securing cloud data that provides a prescriptive solution.
Gartner's Hype Cycle for Data Security in 2022 has defined DSPM.
Why DSPM is the Only Viable Option for business security
DSPM is the only solution that effectively addresses the limitations of traditional and CSP-native solutions. It is purpose-built for cloud data security, with capabilities to identify, classify, and protect sensitive data across the cloud infrastructure. DSPM is also proactive, automating security policies and controls to prevent security incidents before they occur. With DSPM, security teams can confidently enable cloud data practitioners to create value faster and safer than the competition while ensuring compliance with data protection regulations. DSPM is the solution for closing the Security Execution Gap and creating a more secure and productive data environment in the cloud.
Automatically discover and classify data across all cloud environments - One of the biggest challenges for securing cloud data is locating and classifying it. Shadow data stores and abandoned data stores, especially those created for temporary testing or by data scientists and engineers, often fall outside regular security controls. This is why DSPM automates data discovery and classification across all clouds. It benefits security teams by working alongside data and engineering teams to identify and validate all data.
Reduce the attack surface and prevent data exposure in the cloud - DSPM helps security teams minimize cloud data exposure and the associated attack surface by staying in sync with data and engineering teams. The platform automatically identifies data at risk by continuously checking data stores and associated resources for misconfigurations, vulnerable applications, and exposed resources with access to sensitive data.
Track access permissions and enforce least privilege - Inappropriate access permissions can result in the misuse or exposure of sensitive data, either accidentally or through nefarious means. DSPM allows security teams to track data access permissions and enforce the least privilege by providing a simple, accurate view of access privileges for all cloud data stores. This helps IT administrators quickly correct excessive privileges or remove dormant users whose accounts may pose a potential risk to the data.
Continuously monitor for compliance with data security regulations - Compliance audits for data security occur for various mandated laws and regulations. The DSPM platform enables stakeholders to stay ahead of compliance and audit requirements by continuously checking against key benchmarks and associated controls.
Benefits of Deploying DSPM in an Organization

Prevention of Sensitive Data Exposure - In the current digital age, an organization's most critical asset is its data. Deploying a DSPM solution helps protect cloud data from both internal and external threats by identifying all known and hidden or shadow data. DSPM ensures that sensitive data is not exposed and provides a secure environment for organizations to store and manage their data.
Smaller Data Attack Surface - By eliminating unnecessary data, protecting sensitive data becomes more manageable. DSPM solutions identify and remediate all data security violations, ensuring proper controls across an organization's cloud environment. This approach reduces the data attack surface and minimizes the risk of data breaches.
Empowerment of Value Creators - With the ability to automate the validation and enforcement of data security policies, DSPM solutions empower security teams to enable their cloud data users to innovate while ensuring that sensitive data remains secure.
Faster, More Assured Compliance - Organizations face a daunting array of privacy regulations, security, and data frameworks with a data component, including GDPR, HIPAA, CCPA, etc. A DSPM solution can help with compliance by discovering data in the cloud, classifying it, comparing it against data security policies, and driving action.
Reduced Cloud Cost - Storing data in the cloud incurs monthly fees. A DSPM solution helps organizations identify redundant, obsolete, and trivial (ROT) data in their cloud infrastructure. It can be deleted or eliminated to reduce cloud usage fees and the attack surface. Organizations can allocate resources to other critical areas of their business by reducing cloud costs.
What type of DSPM solution should businesses choose?
Here are some key features to consider when selecting a DSPM solution for business:
Agentless data discovery that can connect to multi-cloud environment in minutes and automatically discover all data stores without affecting workload performance.
Cloud-native data classification leverages machine learning and metadata clustering to accurately classify personal, financial, healthcare, developer secrets, and proprietary data.
Security posture management identifies sensitive data assets with weak security postures, including misconfigurations, compliance violations, and logging for business continuity and auditing.
Data access analysis enables users to understand who can take action on specific data and automatically raises timely alerts for security teams when third-party applications gain access to sensitive data.
Data movement detection can detect when data is copied across cloud data stores and define policies to alert when sensitive data is copied or moved between regions, environments, and networks.
Integrations and multi-cloud security that can automatically show data security issues and compliance violations across IaaS, PaaS, and DBaaS.
By considering these features when selecting a DSPM solution, businesses can ensure that they choose a platform that provides complete visibility into data in use, data in motion, and data at rest and helps control data security for all users, devices, and software.
